In 2025, as software development accelerates in complexity and scale, security can no longer be an afterthought. From fintech startups in Bengaluru to government apps in New Delhi, cyber threats are rising in frequency and sophistication. The Indian digital economy, projected to reach $1 trillion by 2030, is a prime target for cybercriminals. In this landscape, DevSecOps — the integration of security into every phase of the DevOps pipeline — is not just a buzzword, but a necessity.
This blog is your go-to guide for understanding and implementing modern software security practices, especially from a DevSecOps perspective, tailored for Indian developers, students, and tech professionals.
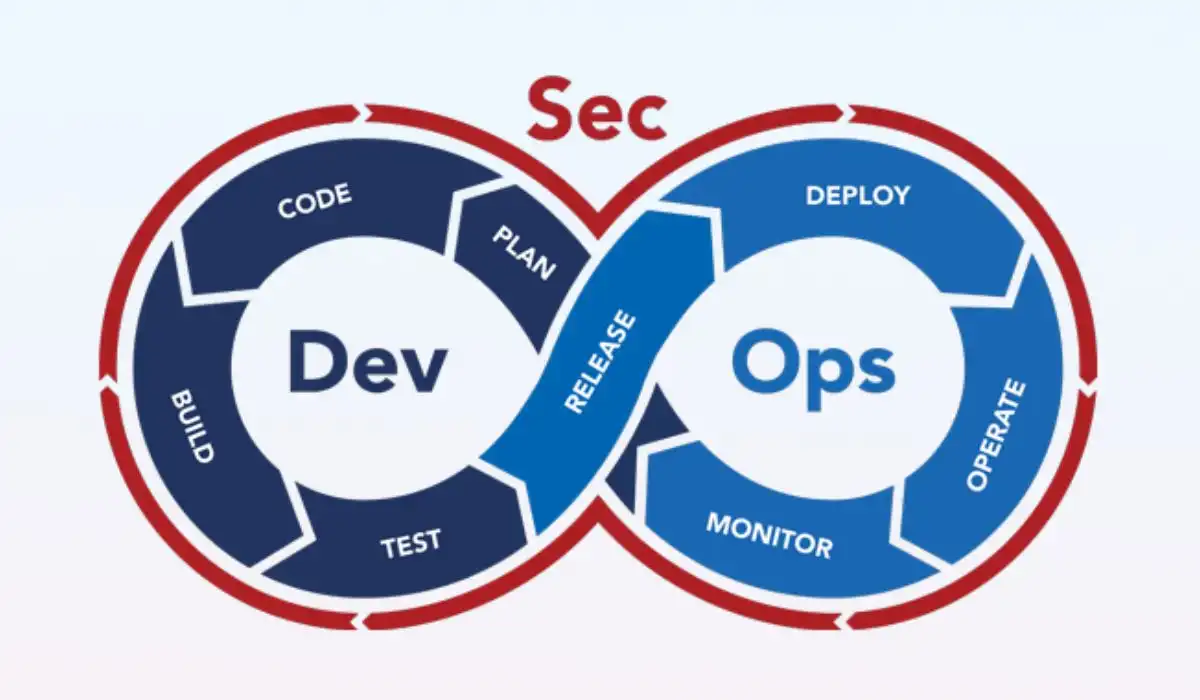
What is DevSecOps?
DevSecOps stands for Development, Security, and Operations — a methodology that embeds security at every stage of the software development lifecycle (SDLC). It ensures that developers, security teams, and operations teams collaborate closely, automating security checks and reducing vulnerabilities before software hits production.
Unlike traditional models where security was addressed at the final stages, DevSecOps shifts security “left”— integrating it from the planning phase.
Why DevSecOps Matters in 2025
- Evolving Threat Landscape: Cyberattacks in India rose by 15% in 2024, with ransomware and supply chain attacks leading the charge.
- Remote and Cloud-Native Development: Post-COVID hybrid models demand robust cloud and API security.
- Regulatory Compliance: India’s Digital Personal Data Protection Act (DPDP Act) mandates stricter data handling and user privacy norms.
Key DevSecOps Best Practices for 2025
1. Start with a Secure Culture
Security is a shared responsibility. Building a secure software product begins with a culture shift:
- Educate developers on secure coding practices.
- Encourage open communication between development and security teams.
- Use Security Champions — developers trained in security who advocate within teams.
Example: A Bengaluru-based edtech startup introduced monthly “Secure Coding Hackathons” — leading to a 40% drop in vulnerabilities.
2. Automate Security in CI/CD Pipelines
Automation is central to DevSecOps. Integrating security checks in Continuous Integration/Continuous Deployment (CI/CD) pipelines ensures early detection of issues.
Tools to Use:
- Static Application Security Testing (SAST): Scans code for vulnerabilities. (Examples: SonarQube, Checkmarx)
- Dynamic Application Security Testing (DAST): Analyzes running applications. (Examples: OWASP ZAP, Burp Suite)
- Software Composition Analysis (SCA): Detects risks in third-party libraries. (Examples: Snyk, WhiteSource)
Tip: Integrate these tools into Jenkins, GitLab, or GitHub workflows for seamless security enforcement.
3. Implement Zero Trust Architecture
Gone are the days of perimeter-based security. In 2025, Zero Trust is the gold standard.
Key principles:
- Never Trust, Always Verify
- Least Privilege Access
- Micro-Segmentation of networks
Example: An Indian fintech company reduced insider threats by implementing Zero Trust, requiring multi-factor authentication for every service interaction.
4. Shift Left with Threat Modeling
Before writing a single line of code, developers should identify potential threats and attack vectors.
- Use STRIDE Model (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to map threats.
- Encourage cross-functional teams to participate in threat modeling exercises.
This proactive approach not only saves cost but also builds resilience.
5. Secure Cloud-Native and Containerized Applications
Most Indian startups now build on Kubernetes, Docker, and AWS/Azure/GCP. These platforms bring agility but also new security risks.
Best Practices:
- Use Infrastructure as Code (IaC) security scanning (e.g., Checkov, TFLint)
- Scan containers for vulnerabilities before deployment
- Apply Pod Security Policies and Network Policies in Kubernetes
- Encrypt data at rest and in transit
Stat: 94% of Indian IT firms adopted containerized deployments in 2024, but only 58% had proper container security policies.
6. Monitor Continuously and Respond Rapidly
Security is not a one-time task — continuous monitoring and incident response planning are vital.
What to Monitor:
- Unauthorized access attempts
- API anomalies
- Performance deviations
Tools to Use:
- SIEM (Security Information and Event Management): Splunk, ELK Stack
- EDR (Endpoint Detection and Response): CrowdStrike, SentinelOne
Also, maintain an Incident Response Plan with clear roles, communication plans, and recovery procedures.
DevSecOps Challenges in India – And How to Overcome Them
| Challenge | Solution |
| Lack of trained security talent | Conduct internal workshops; use open-source training (OWASP) |
| Budget constraints | Use free/open-source tools like ZAP, Trivy |
| Resistance to change | Demonstrate ROI by reducing post-release bugs |
Final Thoughts: Future of Software Security in India
Securing your software in 2025 is not just about installing tools or running scans. It’s about building a mindset that embraces security from day one. For Indian developers and companies, this means aligning with global standards while considering local regulations and realities.
Whether you’re a B.Tech student in Hyderabad, a backend developer in Pune, or a startup founder in Gurugram — understanding and implementing DevSecOps practices can set you apart. The sooner you build secure habits, the more resilient your applications – and your career – will be.
Read Also: The Rise of Edge Computing: Building Faster & More Secure Apps Near the User
Summary: Best Practices Checklist
- Foster a security-first culture
- Integrate SAST, DAST, SCA into your CI/CD
- Adopt Zero Trust architecture
- Model threats early in development
- Secure cloud-native and containerized environments
- Continuously monitor and have an incident response plan
Stay ahead. Stay secure. Your software – and your users – deserve nothing less.